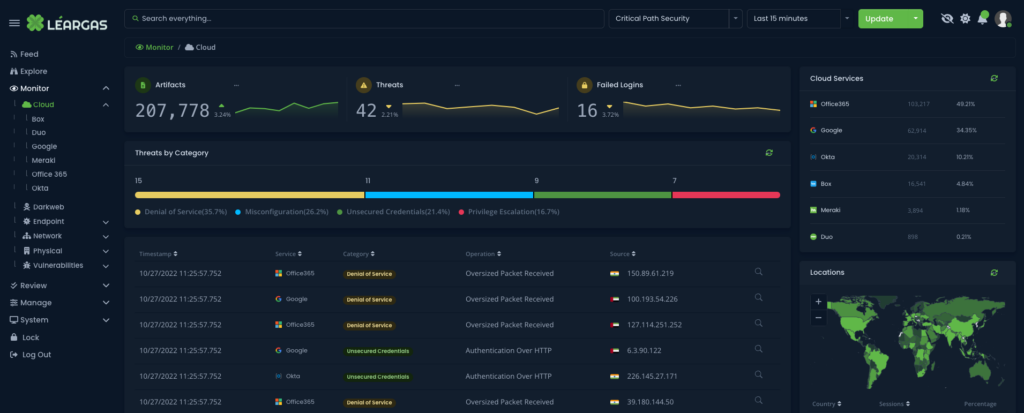
As organizations adapt to the ever-changing cyber threat landscape, they increasingly depend on threat intelligence feeds to remain informed about the latest malicious activities and safeguard their digital assets. These feeds provide real-time, actionable information on a variety of cyber threats, encompassing elements such as IP addresses, domains, malware hashes, and email addresses. However, the very resource designed to protect an organization can also become its Achilles’ heel when threat actors poison these feeds, potentially compromising networks and systems. In this blog post, we delve into the significance of proper curation and validation of artifacts as a means to counter the risks linked to threat intelligence feed poisoning.
Continue readingResponsible Usage of ChatGPT in Large Organizations: Ensuring Ethical and Secure AI Practices
Artificial Intelligence (AI) has made significant advancements in recent years, with ChatGPT by OpenAI emerging as one of the most popular language models. Its potential to enhance productivity and efficiency across a wide range of tasks is undeniable. However, as large organizations increasingly adopt this technology, it is essential to ensure responsible and ethical usage. In this blog post, we discuss the key points to consider when using ChatGPT in a large organization, focusing on security, reliability, and ethical concerns.
Continue readingLéargas Security with AI – The Dawn Of A New Age In Cybersecurity
For a long time, “artificial intelligence” has been a popular buzzword in the cybersecurity sector, boasting solutions capable of detecting suspicious network activities, rapidly understanding the situation, and assisting in incident response upon an intrusion. However, the most effective and reliable services so far have been machine learning algorithms designed to identify malware traits and other questionable network behaviors. Now, with the increasing availability of generative AI tools, Léargas Security has finally developed a service for security professionals that lives up to the hype.
Continue readingLéargas Security Sponsors NRECA 2023 Co-op Cyber Tech
Léargas Security, a leading cybersecurity firm, has made a name for itself by providing top-notch security solutions and services to clients worldwide. With a focus on innovation, Léargas Security stays ahead of emerging threats by continuously updating its strategies and techniques. The company’s dedication to excellence has made it the perfect partner for NRECA in the 2023 Co-Op Cyber Tech Conference.
Continue readingLéargas Security with AI: The Cost Factor
With the increasing number of cyber-attacks and the ever-changing threat landscape, there is a growing demand for cybersecurity analysts who can effectively protect computer systems and networks. However, the shortage of skilled cybersecurity professionals is a major challenge that many organizations face. Artificial Intelligence (AI) has emerged as a potential solution to this problem, and its importance in the strategic shortening of skills gaps in cybersecurity analysts cannot be overstated. That is why Léargas Security has leveraged ChatGPT for strategically shortening the knowledge gap.
Continue readingLeveraging ChatGPT To Close The Knowledge Gaps
Cybersecurity threats are increasingly becoming more frequent, sophisticated, and complex, and companies are struggling to keep up with the pace. With the rise of the internet, the number of attacks has grown exponentially, and attackers are continuously finding new ways to bypass traditional security measures. As a result, the demand for security analysts has increased drastically, however, there is a significant shortage of qualified professionals to fill these positions.
Continue readingWhat Is SecOps and What Is The Value Of SecOps To Organizations?
The Importance of Normalization and Scoring of Threat Intelligence Artifacts
In the present-day, interconnected world, businesses confront an expanding threat landscape. To safeguard themselves from cyber threats, organizations rely on threat intelligence, which is one of the most valuable tools available. However, the effectiveness of threat intelligence hinges on the quality of its data. That’s why normalization and scoring of threat intelligence artifacts are two indispensable procedures that guarantee high-quality data.
Continue readingVisibility and Log Fidelity – Recommendations
Inline Detections and Hunting: The Differences and Value Gained
The threat landscape is continually evolving and growing increasingly complex, therefore organizations must take a proactive approach to cybersecurity. Traditional security tools such as firewalls, intrusion detection systems (IDS), and antivirus software are no longer sufficient to protect against advanced threats. Inline security detections and threat hunting are two approaches that can help organizations to better detect and respond to security threats.
Continue reading