In today’s digital age, cybersecurity is more critical than ever before. With the growing number of cyber threats, it is essential to reduce the attack surface to protect your organization’s assets. What is the “attack surface”? The attack surface refers to the total number of vulnerabilities, entry points, and possible attack vectors that hackers can exploit to gain unauthorized access to an organization’s systems and data. In this blog post, we will discuss the importance of reducing the cybersecurity attack surface and some effective ways to do it.
Continue readingThe Importance of Artificial Intelligence and Machine Learning in Cybersecurity
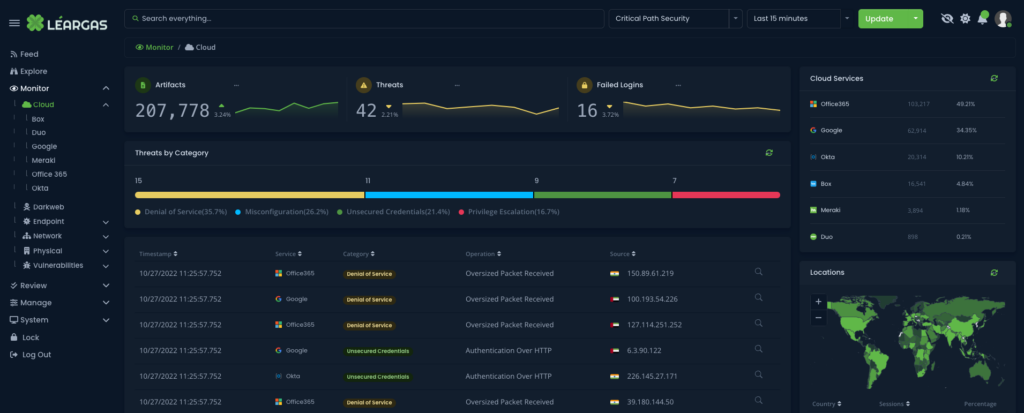
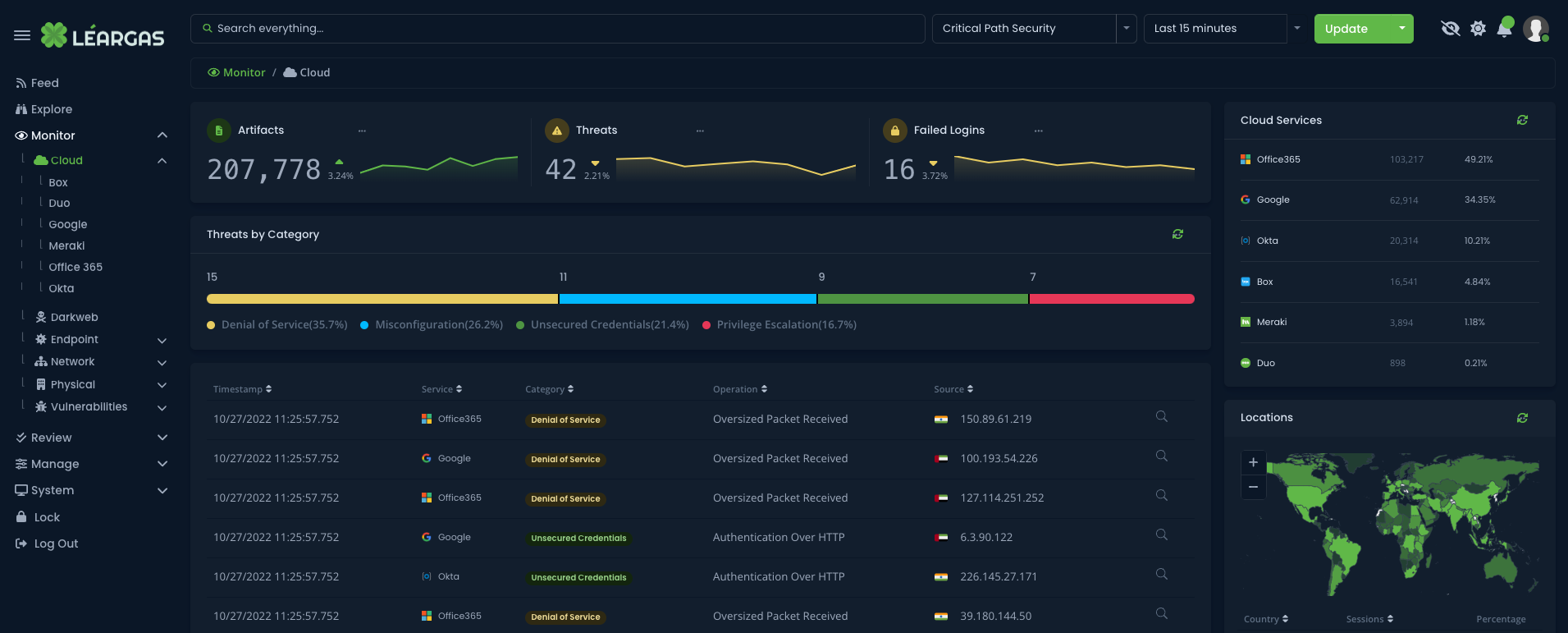
Léargas Security, like many other Extended Detection and Response (XDR) platforms, has become an essential part of modern cybersecurity. As the number and complexity of cyber threats continue to increase, more organizations are turning to Léargas to provide comprehensive and proactive threat detection and response capabilities. And one of the most significant advancements in the Léargas platform in recent years has been the integration of artificial intelligence (AI) and machine learning (ML) algorithms.
Let’s understand what Léargas is. Léargas is an advanced security platform that provides organizations with a comprehensive approach to threat detection and response. Unlike traditional security solutions that only focus on specific parts of an organization’s infrastructure, the Léargas platform leverages data from multiple security tools and data sources, both on-premises and in the cloud, to provide a more holistic and comprehensive view of the network, endpoints, and cloud environments. The Léargas platform combines security analytics, threat intelligence, and automated response capabilities to detect and respond to threats across the entire infrastructure.
With the integration of artificial intelligence and machine learning, Léargas can improve the detection capabilities and speed up response times for its subscribers. Artificial intelligence and machine learning algorithms can process copious amounts of data from a growing number of sources in real-time, identifying patterns and anomalies that may indicate an attack. This allows the Léargas platform to detect and respond to threats more quickly, reducing the risk of damage and data loss.
So, here are some specific ways that the Léargas platform utilizes AI and ML:
- Enhanced detection capabilities: AI and ML algorithms can analyze large volumes of data from various sources, such as network traffic, logs, and endpoints. This enables Léargas to detect advanced and emerging threats that traditional security solutions may miss.
- Faster response times: AI and ML algorithms can automate response actions, such as isolating infected endpoints, blocking malicious traffic, and containing the attack. This permits Léargas to respond quickly to threats, reducing the time-to-detection and time-to-response.
- Reduced false positives: AI and ML algorithms can filter out false positives, reducing the number of alerts that security teams need to investigate. This saves time and resources, allowing security teams, both MSP (Managed Service Providers), MSSP, and independent organizations to focus on more critical threats.
- Improved threat intelligence: AI and ML algorithms can analyze threat intelligence data, identifying new patterns and trends that may indicate emerging threats. This enables Léargas to stay ahead of the threat landscape, providing proactive threat detection and response capabilities. Additionally, Léargas partners with companies like Critical Path Security to gain more valuable intelligence each day.
- Better risk management: AI and ML algorithms can provide risk scoring and prioritization, allowing security teams to focus on the most critical threats.
- Malware analysis: Machine learning algorithms are used by the Léargas platform and the supported EDR (Endpoint Detection and Response) solutions to analyze malware behavior, identifying patterns that may indicate the presence of malware, ransomware, or an internal threat actor on a network.
Léargas strives to secure organizations by enhancing threat detection capabilities, speeding up response times, reducing false positives, improving threat intelligence, and providing better risk management.
As the threat landscape continues to evolve, organizations need advanced security solutions that can keep pace with the changing threat landscape. The AI-powered Léargas security platform provides a proactive and comprehensive approach to cybersecurity, helping organizations to stay one step ahead of cyber threats.
Correlation and Enrichment: Office365 and Endpoint Security
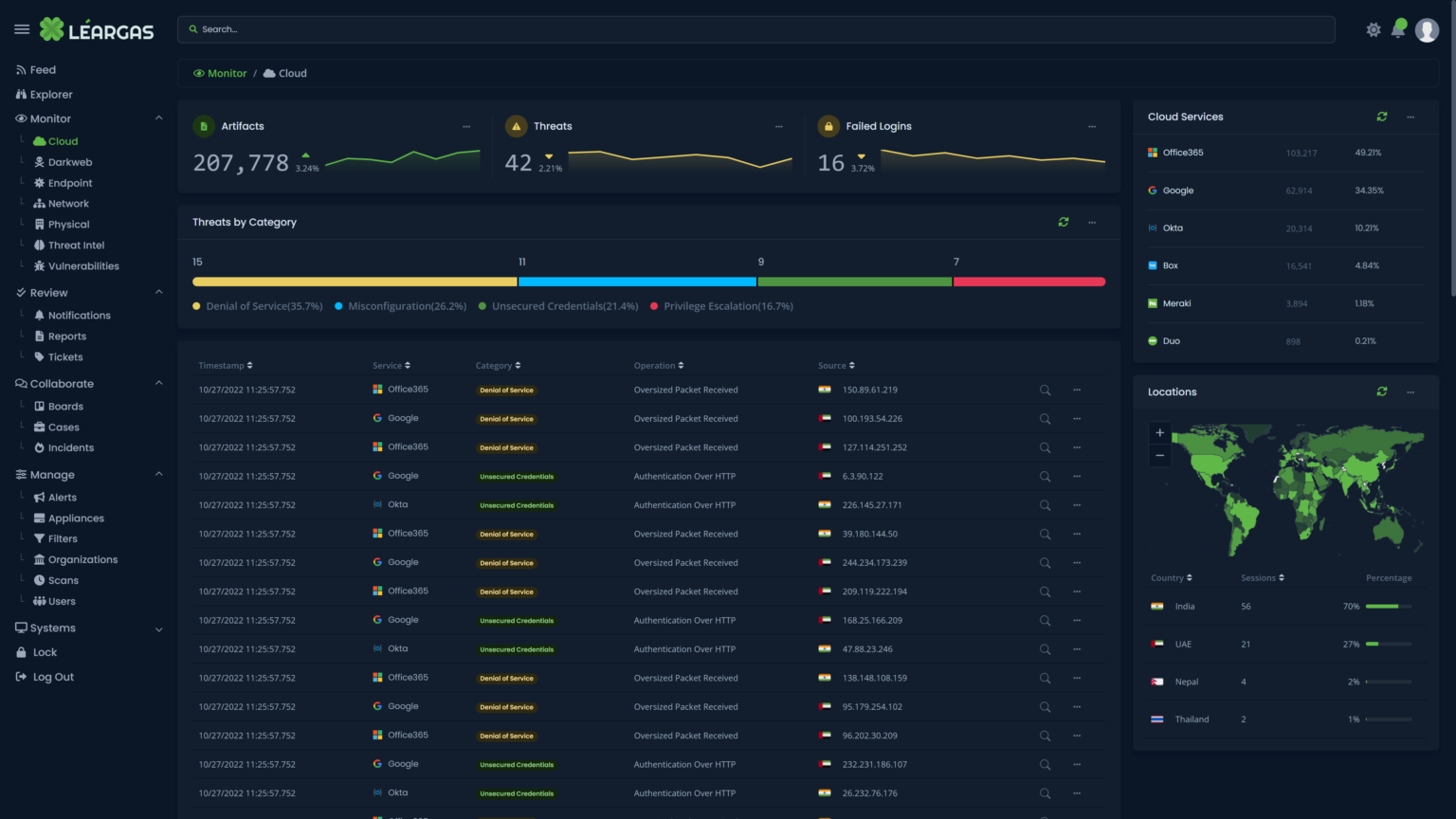
As organizations increasingly rely on cloud-based services such as Office 365 for their productivity and collaboration needs, it’s critical to understand the importance of correlating logs from both the cloud service and the endpoint devices. This correlation can provide a comprehensive view of the activities taking place within the organization and help ensure the security and compliance of sensitive information, no matter where the endpoint might be.
One of the main benefits of correlating Office 365 and Endpoint Security logs is that it can help identify suspicious or malicious activity. For example, if a user’s endpoint device shows signs of a security breach, geographically-impossible authentication attempts, or attacks such as a virus or malware event, the corresponding Office 365 logs can provide valuable information on what data may have been accessed or exfiltrated.
The Léargas Security platform automatically correlates the data from the sources into single searches and alerts.
Additionally, correlating Office 365 and Endpoint Security logs can also help organizations identify compliance violations, such as unauthorized access to sensitive information. With the right tools, organizations can quickly identify when a user has taken actions that violate their data protection policies, such as downloading confidential data onto a personal device or sending sensitive information to an unauthorized email recipient.
Moreover, correlating logs can help improve incident response time. In the event of a security incident, having a comprehensive view of the activities that took place can help organizations quickly identify the source and scope of the problem, enabling them to respond and resolve the issue more efficiently.
Here are the Top 10 reasons for automatically correlating Office 365 and Endpoint Security logs:
- IMPROVED VISIBILITY INTO USER ACTIVITY: Correlating logs provides a comprehensive view of what users are doing within the organization, including access to sensitive information and email correspondence, regardless of location and time.
- DETECTING SUSPICIOUS OR MALICIOUS ACTIVITY: Correlating logs can help identify potential security threats and unauthorized access to sensitive data.
- IMPROVING INCIDENT RESPONSE TIME: Having a comprehensive view of activities can help organizations quickly identify the source and scope of security incidents, allowing them to respond more efficiently.
- ENSURING COMPLIANCE WITH INDUSTRY REGULATIONS: Organizations can use log data to demonstrate compliance with regulations such as GDPR and HIPAA.
- AUDITING AND COMPLIANCE REPORTING: Log data can provide valuable insights for auditing and compliance reporting, helping organizations ensure that their security and privacy practices are up to standards.
- PROTECTING SENSITIVE DATA: Correlating logs can help organizations identify when sensitive data is being accessed, downloaded, or sent to unauthorized recipients, allowing them to take appropriate action to protect it.
- DETECTING ENDPOINT SECURITY BREACHES: Endpoint devices are a common target for attackers, and correlating logs can help organizations identify when a device has been compromised and what data may have been accessed.
- IDENTIFYING UNUSUAL USER BEHAVIOR: Correlating logs can help organizations identify when users are engaging in suspicious or unusual behavior, allowing them to take appropriate action to mitigate potential threats.
- DETECTING DATA EXFILTRATION: By tracking user activities, organizations can identify when sensitive data is being exfiltrated and take appropriate action to prevent it.
- ENHANCING SECURITY AND PRIVACY: By correlating logs, organizations can gain a better understanding of their security and privacy practices and take appropriate steps to improve them.
Finally, correlating Office 365 and Endpoint Security logs can also provide valuable insights for auditing and compliance reporting. Organizations can use the data from these logs to demonstrate their compliance with industry regulations and standards, such as GDPR and HIPAA, by providing a detailed view of their security and privacy practices.
Zeek vs NetFlow: Why Léargas chose Zeek

As organizations continue to rely more on networked systems for critical operations, the need for efficient and effective network traffic analysis solutions becomes increasingly important. Two popular solutions for network traffic analysis are Zeek and Netflow, and many organizations are faced with the challenge of choosing between the two. In this blog post, we will take a closer look at each solution and explore why we are proudly built on Zeek.
What is Zeek?Zeek is a powerful and flexible open-source network security monitoring tool that provides a rich set of features for network traffic analysis. Zeek operates by capturing network packets and creating logs of network activity in real-time. These logs provide detailed information about network connections, protocols, and other relevant data, making it an ideal solution for security professionals who need to quickly identify security threats and respond to incidents. What is Netflow?
Netflow is a network traffic analysis protocol that was developed by Cisco Systems. Netflow provides a method for collecting information about network traffic and analyzing it to identify trends, anomalies, and other important information. Unlike Zeek, which focuses on analyzing network packets, Netflow focuses on analyzing network flow data, which is a high-level view of network activity. Netflow is well-suited for organizations that want to get an overview of network traffic patterns without getting into the technical details of packet analysis. Zeek vs Netflow: Pros and Cons
Zeek and Netflow each have their own strengths and weaknesses, and the solution that is best for you will depend on your specific needs and requirements.
Pros of Zeek:
- Network traffic analysis and inspection
- Intrusion detection and threat hunting
- Integrated Threat Intelligence
- Embedded File Extraction and Analysis
- Protocol analysis and decoding
- Flexible logging and reporting
- Customizable and extensible scripting
- High-performance and scalability
- Integration with other security tools
- Advanced analytics and data visualization
- Flexible deployment options (e.g. standalone, cluster, cloud)
Cons of Netflow:
- Limited in terms of the data it provides compared to Zeek
- May not provide enough detail for advanced network security analysis
- Does not provide real-time analysis
Choosing between the Zeek-based, Léargas Security platform over Netflow-based platforms for network traffic analysis is an easy decision.
If you’re looking for a solution that provides a rich set of features for network traffic analysis, real-time analysis of network packets, and the ability to identify security threats and respond to incidents quickly, then the Zeek-based, Léargas Security is the solution for you.
With the right solution in place, you can ensure that your network is secure and that you have the information you need to quickly respond to security incidents.
What is SOAR and how can it help you?

What is SOAR and how can it help you?
SOAR (Security Orchestration, Automation, and Response) is a technology that enables security teams to automate repetitive tasks, aggregate multiple security tools and technologies into one unified platform, and improve the speed and accuracy of incident response. It helps organizations to streamline their security operations and make them more efficient and effective.
SOAR and platforms such as Léargas Security can perform tasks such as:
- Automating routine and repetitive tasks, freeing up security teams to focus on more complex incidents.
- Integrating with other security tools, such as SIEMs, firewalls, and endpoint protection solutions, to gather data and automate incident response.
- Correlating and analyzing data to quickly identify potential threats and prioritize incidents.
- Providing a centralized and standardized incident response process to improve the speed and efficiency of response efforts.
- Documenting and reporting on security incidents to improve incident response and to meet compliance requirements.
How does this differentiate from a SIEM?
SIEM stands for Security Information and Event Management, and is a type of software that collects and analyzes security data from various devices on a network to provide a centralized view of security events and to identify potential security threats. SIEMs help organizations to comply with security regulations, detect and respond to security incidents, and monitor the security posture of their networks.
SIEM and SOAR are both security technologies, but they serve different purposes and have different focuses.
SIEMs are designed to collect, store, and analyze security-related data from various sources such as network devices, servers, and applications. The goal of SIEMs is to provide a centralized view of security events and to help detect and respond to potential security threats.
Léargas Security, on the other hand, is designed to automate and orchestrate security-related processes such as incident response, threat hunting, and vulnerability management. Léargas Security provides a platform for security teams to automate repetitive tasks, standardize incident response procedures, and improve the overall efficiency of the security operations.
In summary, organizations may choose Léargas Security that leverages SOAR technology over a SIEM, because Léargas Security offers a more comprehensive and integrated approach to threat detection and response that covers multiple environments, while other platforms are limited to a narrower scope of security events and data.
Will ChatGPT Change Cybersecurity?
 The leading question around the Cybersecurity community has been, “Will ChatGPT and OpenAI change Cybersecurity?“.
The leading question around the Cybersecurity community has been, “Will ChatGPT and OpenAI change Cybersecurity?“.
It’s a great question, as those technologies are far more advanced than most of us expected them to be at this point in time. The answer is, “We aren’t entirely sure, but we have an idea.“.
Even asking ChatGPT for the answer is met with some ambiguity.
“It is possible that ChatGPT or similar language models may be used in the field of cybersecurity in the future. For example, they could potentially be used to generate more realistic and diverse phishing or malware attacks, or to assist in analyzing large volumes of text-based data such as logs or email communications. However, it’s important to note that these models are not inherently malicious and their use in cybersecurity would depend on how they are implemented and controlled by organizations.”
Anyone that has spent time around machine learning or data modeling will agree that all data used to build those models is historical, because that’s how data works. You can’t collect it until it has happened. This understanding helps frame up the possibilities around the potential of ChatGPT and OpenAI.
Created predictions aren’t binary, meaning a “yes” or a “no”, but made in “varying degrees of confidence”.
So, knowing that it can’t do all of the things, let’s look at some of the things that it can, and often, won’t do.
Offensive Capabilities
- Phishing – It will not automatically write a phishing email. Protections are in place to dissuade the use of the platform for malicious uses. Yes, some protections can be bypassed, but as new tactics are attempted, new protections are put in place.
- Social Engineering – ChatGPT will create content that could be used in a social engineering campaign, but the effectiveness of that content still comes down to the creativity of the threat actor. It will not fully automate a social engineering campaign.
- Malware Generation – ChatGPT will happily write an Ansible playbook or other remote management program that can be used in Malware. However, it will not create new vulnerabilities and requests to do so respond with how to defend a system against a particular class of vulnerabilities.
Defensive Capabilities
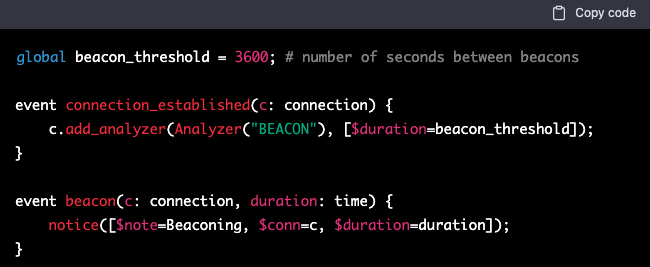
Also, it can build defenses.
- Zeek Behavioral Detections – ChatGPT can create detections for malicious events that could occur on networks, such as this detection for beaconing. Beaconing is a common indicator of a successful ransomware event.
- Windows Event Log Detections – ChatGPT will create detections that will search the Security event log for events that correlate with specific event IDs, then filters the events that occurred in the past day and checks if any events match the criteria. If any events are found, it will output a warning message and display the matching events. Otherwise, it will output a message saying that no suspicious activity was detected.
- Email Phishing and Ransomware Detections – ChatGPT will build a detection looks for specific keywords in the subject, sender, and body of an email. If the email contains “urgent”, “bank”, “click here”, “password”, and “account” in those fields, it will trigger the detection and print a message indicating that a phishing email has been detected.
As we continue the conversation around ChatGPT and the potential impacts it might have, let’s not lose focus on the positives of this incredible innovation. As shown above, ChatGPT currently provides more positive impact than negative.
Why should I use Léargas Security for data leak detection?
 Data leak detection is a technology that helps organizations identify and prevent the unauthorized disclosure of sensitive or confidential information. Léargas automates this process, by leveraging artifacts collected from live network traffic, and automatically scouring data leak sites for those artifacts. Using Natural Language Processing, discovery of data leaks can extend to nearly any part of the open web and dark web, even into social media.
Data leak detection is a technology that helps organizations identify and prevent the unauthorized disclosure of sensitive or confidential information. Léargas automates this process, by leveraging artifacts collected from live network traffic, and automatically scouring data leak sites for those artifacts. Using Natural Language Processing, discovery of data leaks can extend to nearly any part of the open web and dark web, even into social media.
So, why should your organization leverage this service?
- Monetary Damage: Leaks of sensitive Intellectual Property, have become increasingly more common. With sensitive leaked information and more from Twitter, LastPass, Slack, WhatsApp, InfraGard, it’s clear that no one is immune to a data leak.
- Compliance: Many industries have strict regulations around the handling of sensitive information, and a data leak can result in significant fines and other penalties. Data leak detection can help organizations stay compliant by identifying and preventing unauthorized disclosures of sensitive information.
- Reputation: A data leak can damage an organization’s reputation, especially if it involves sensitive information such as customer data or financial records. Data leak detection can help organizations protect their reputation by identifying and preventing leaks before they occur.
- Security: Data leaks can also compromise an organization’s security, especially if they involve sensitive information such as passwords or login credentials. Data leak detection can help organizations to identify and prevent these types of leaks, which can help to protect against cyber attacks and other security breaches.
- Cost: Data leaks can be costly, both in terms of the financial impact and the time and resources required to investigate and fix the problem. Data leak detection can help organizations identify and prevent leaks before they occur, which can help reduce the overall cost of data breaches.
With Léargas, data breach and leak detection is not a new service, platform, or product, that acts as an extension of your current defenses. The Léargas service is integrated and tied to the existing data flows and logs.
No extra keys.No extra reports.
Just results. Try Léargas Today!
Why Do You Need The Léargas Security Platform?
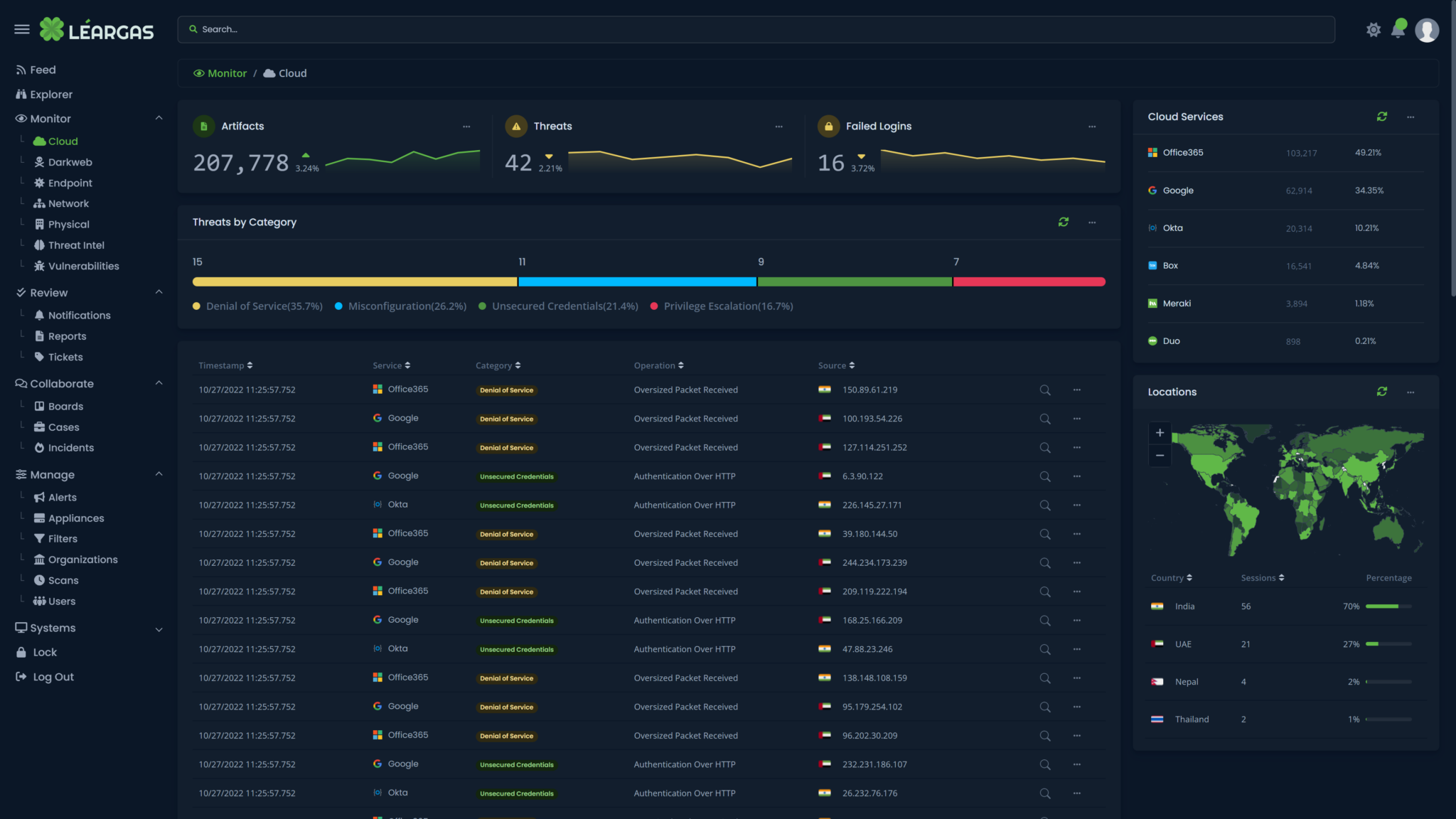
iLéargas Security brings a proactive approach to threat detection and response. It delivers visibility across all data, including endpoint, network, cloud, and physical security data, while applying analytics and automation to address today’s increasingly sophisticated threats.
With the Léargas Security platform, cybersecurity teams can:
- Track threats across any source or location within the organization, using Zeek, Suricata, EDR, and nearly any log source available.
- Apply threat intelligence and behavioral-based detection across all sources of information, including Critical Path Security’s threat intelligence feeds.
- Track threats across any source or location within the organization, as well as in the cloud.
- Increase the productivity of the people operating the technology, by leveraging machine learning and artificial intelligence to rule out “false positives”.
- Get more out of their security investments, by consolidation.
The Léargas Security platform enables organizations to prevent successful cyberattacks, improve their security posture, and reduce risk, as well as simplify and strengthen security processes, through a seamless user interface that incorporates all physical and cyber intelligence.
Benefits –
- Block attacks with endpoint protection with wire-level analysis: Block malware, exploits, and file-less attacks with integrated antivirus and real-time file analysis on the wire. No endpoint agent? No problem.
- Gain visibility across all your data sources: Collect and correlate data from any source to detect, triage, investigate, hunt, and respond to threats.
- Automated reports: Daily Security Log Review (DSLR) reports are automatically generated and provided to the team for daily review and record keeping.
- Increase productivity: Consolidate security policy management and monitoring, investigation, and response across your physical, network, endpoint, and cloud environments in one pane of glass.
- Shut down persistent advanced threats: Protect your network against insider attacks, extortion, ransomware, file-less and memory-only attacks, and zero-day malware.
- Reduce fatigue and potential lost artifacts: Case management integration will directly integrate into Incident Response Platforms, such as IRIS, ServiceNow, and CyberCPR.
- Trace malicious behavior from the badge swipe to the data exfiltration: Léargas Security correlates all behaviors that permits teams to get to the root cause of security events.
Elastic showcases Léargas Security!
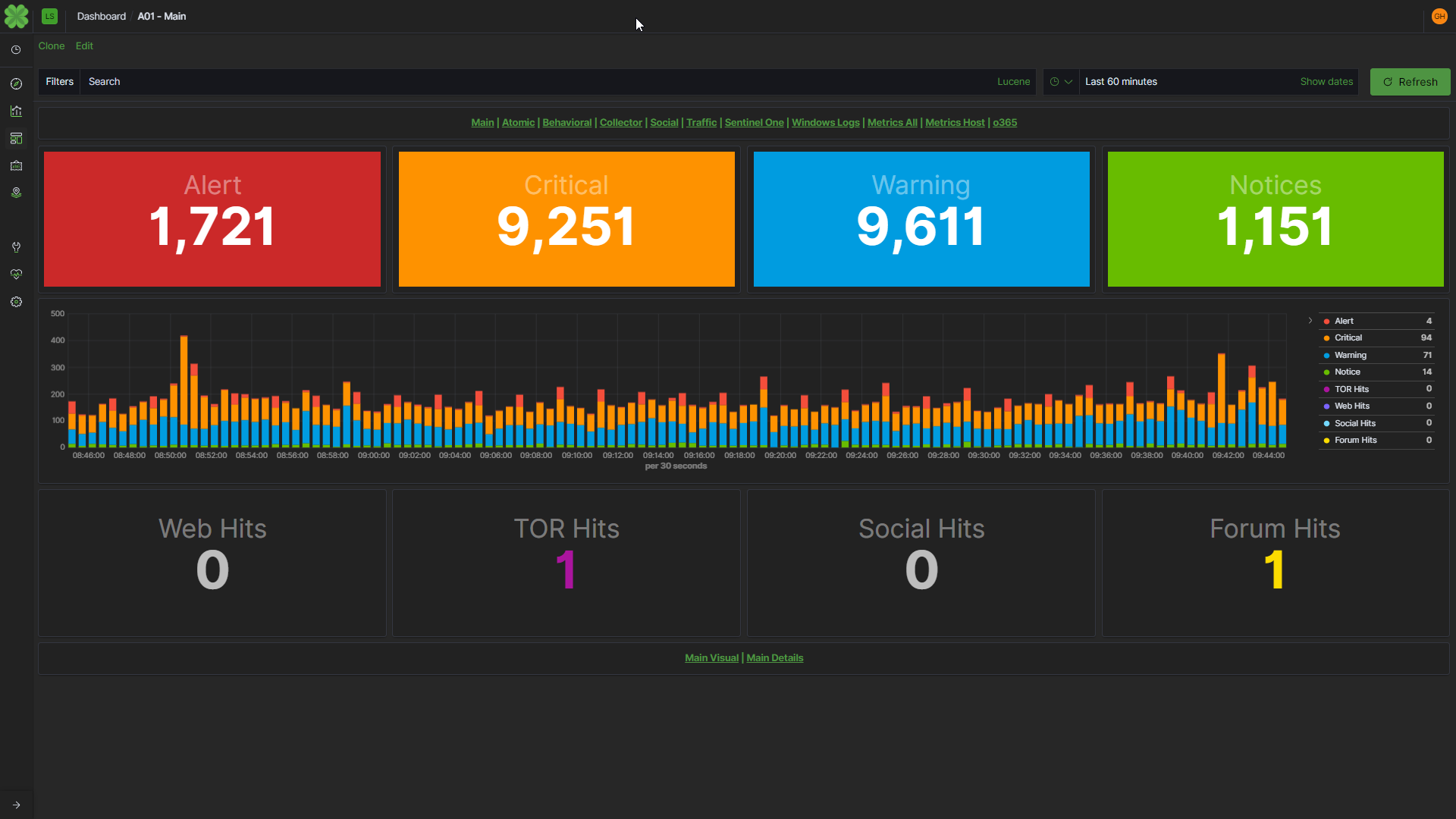
Léargas Security (Léargas is Gaelic for “insight”) provides clients with actionable insights into anomalous or abstract behaviors through the correlation of data gathered from converged security controls: cyber and physical.
Our company carries the concept of actionable, converged data even further with natural language processing and correlation of dark web, social media, TOR, chan, and additional sources in near real time to expose indicators of compromise and threats against customers and partner organizations.
https://www.elastic.co/blog/leargas-security-chooses-elastic-drops-splunk-to-battle-covid-19-fraud
Real-time Correlation with Vulnerability Scan Metrics
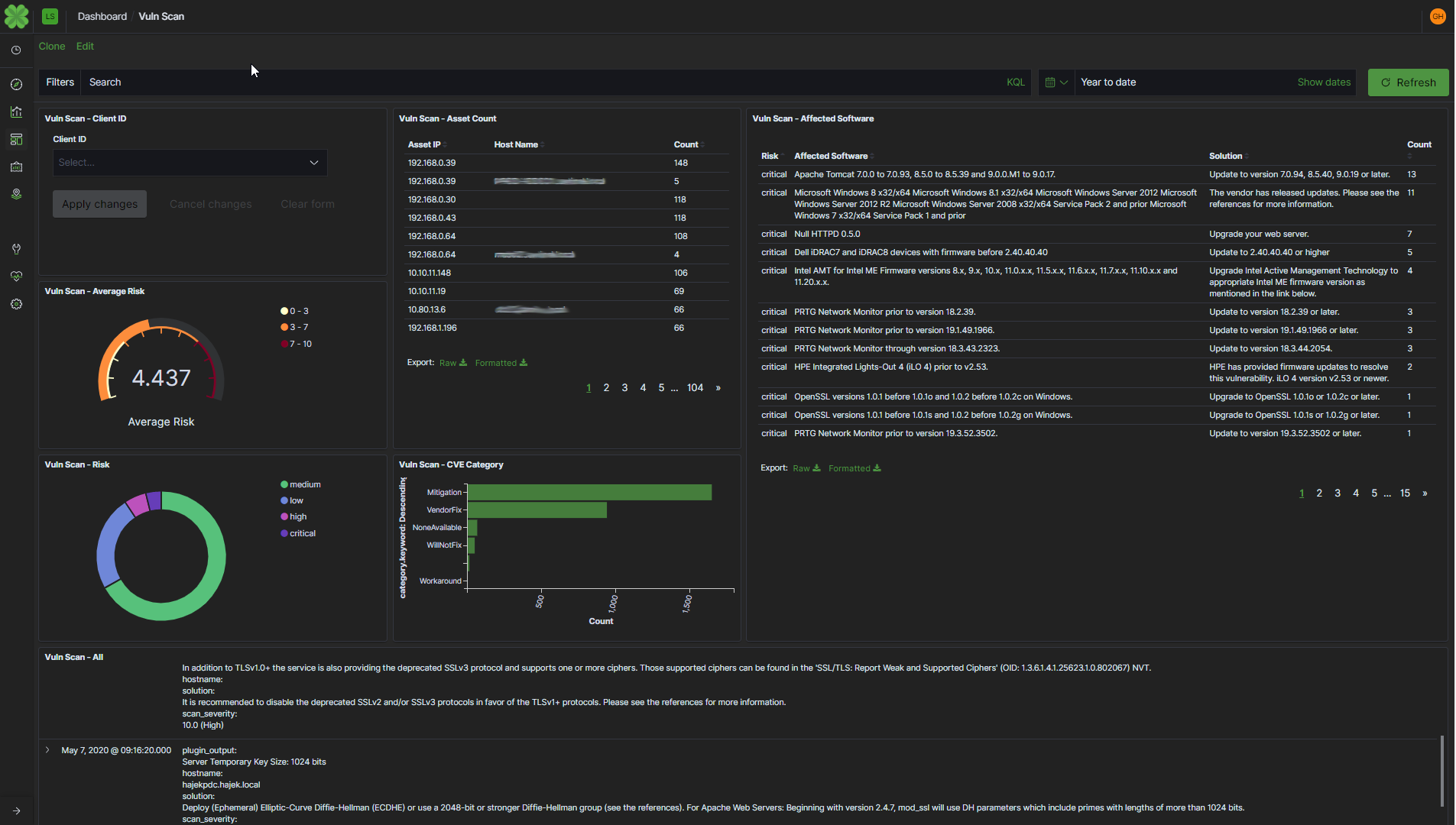 Léargas Vulnerability Telemetry
Léargas Vulnerability Telemetry
Léargas is proud to announce its latest platform enhancement; Real-time Correlation with vulnerability scans to further increase the accuracy and confidence of alerts.
Data correlation has always been at the heart of Léargas, and this added functionality makes use of the platform’s foundation to tag alerts and notices on the fly with relevant information from the latest vulnerability scans.
This feature has reduced the number of false positives and increased overall confidence in our notifications and alerts. Additionally, this information becomes immediately available to drive next steps in our escalation and remediation process, enhancing network security and further reducing dwell time of attacks.
Just another way Léargas is providing insight.