Léargas has always been about providing “Insight”. Now, it fights for the world!
Global events such as the Coronavirus (COVID-19) make all of us targets for cybercriminals. It could be in the form of phishing emails or new targeted scams, these tactics are meant to take advantage of individuals who are understandably concerned about their health and safety of their family during this challenging time.
Additionally, it targets companies that have effectively turned their infrastructure “inside-out” to provide all of the necessary services and data for their now remote-workers to perform at their best. That means weakened firewall rules, mission-critical servers connected to the Internet, and no multi-factor authentication.
This pandemic is challenging for all of us. We all need to adapt to this new reality and look out for one another any way we can. Our mission with Léargas has always been to protect people against threats at the intersection of cyber and the physical world, and this disaster has provided us with the motivation to find new ways to help.
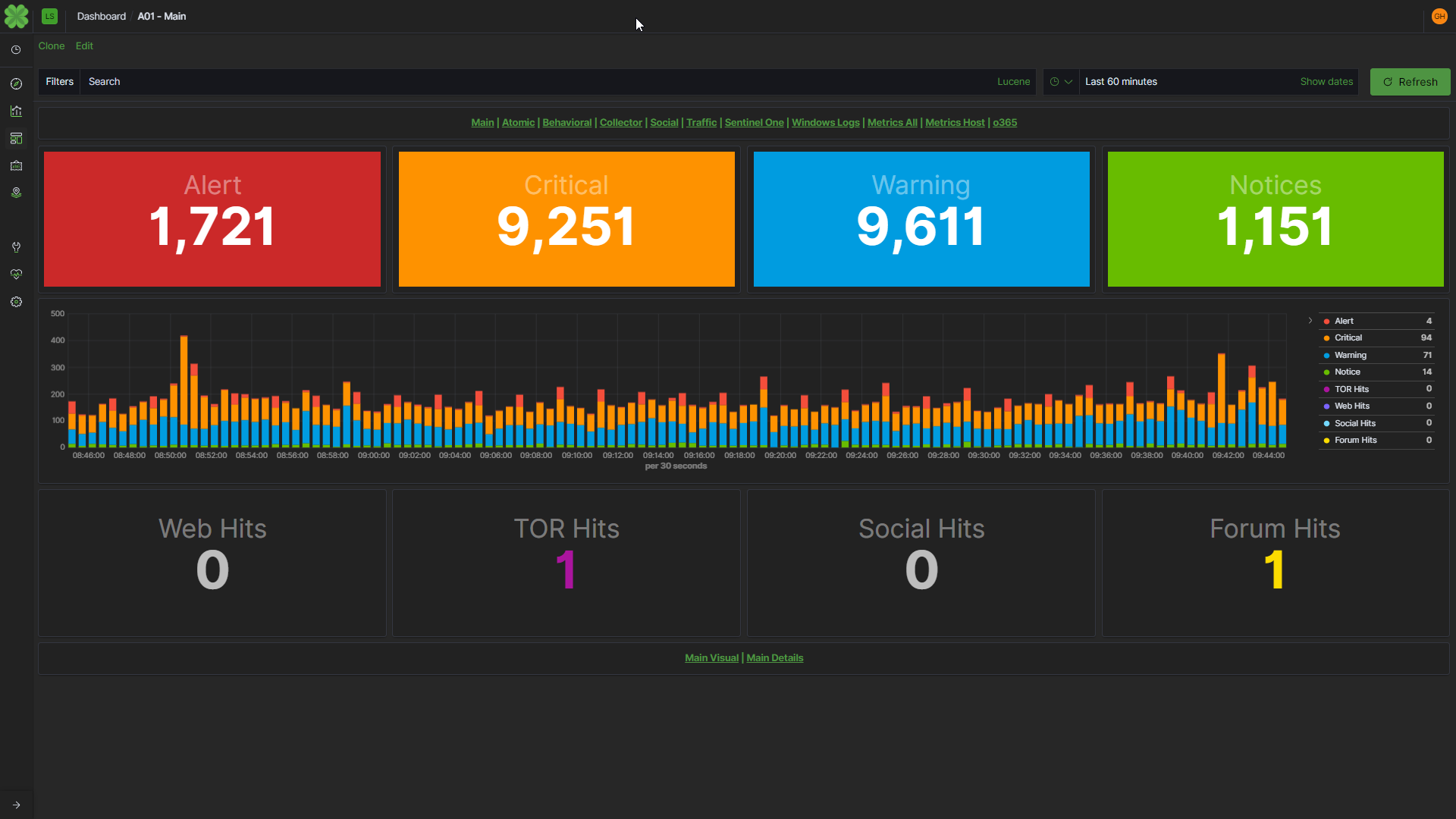
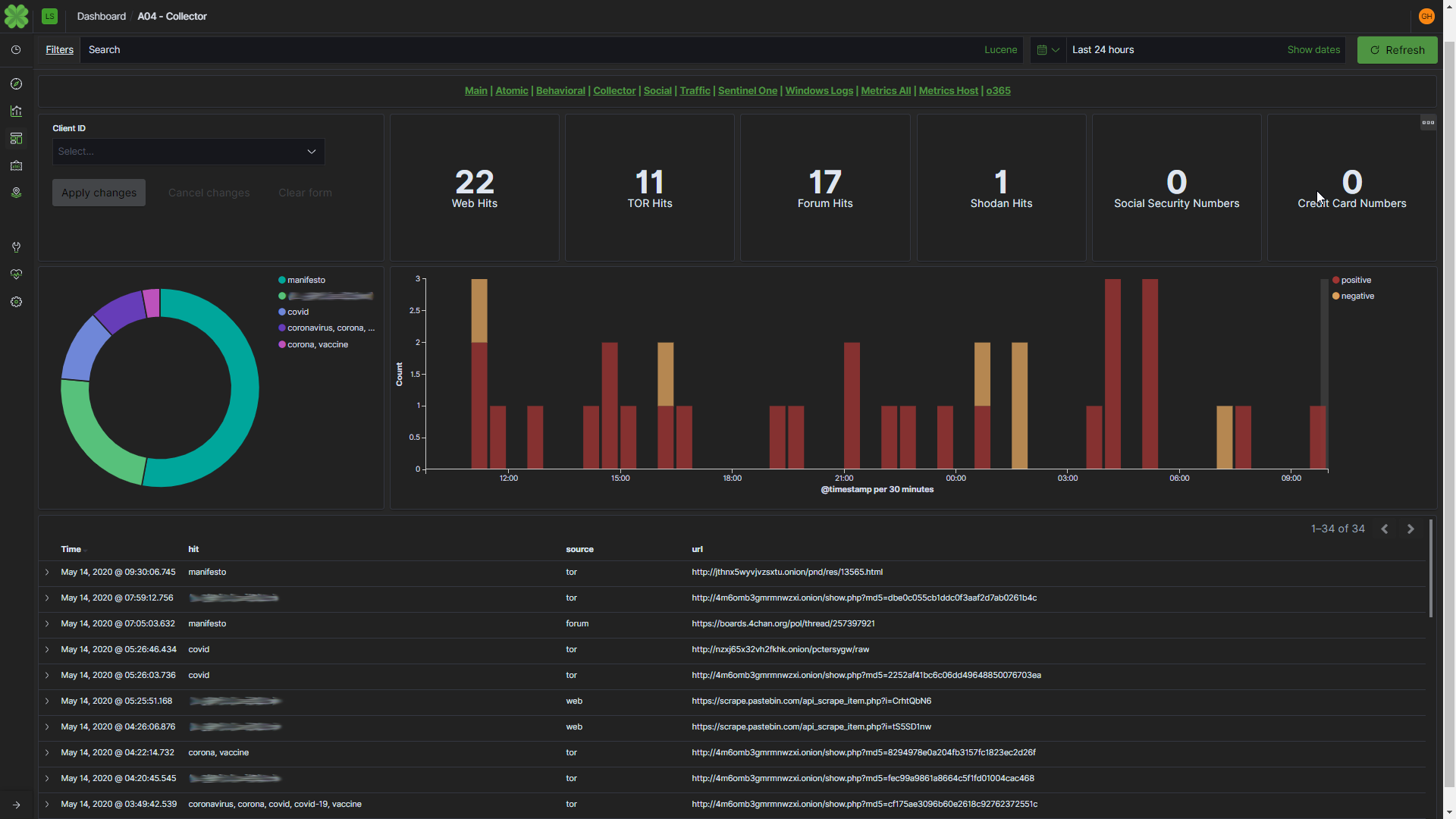
As with any new endeavor, knowledge is key, so we began ingesting atomic indicators around COVID-19/Coronavirus and converting them into an actionable data set for the mitigation of COVID-related digital threats.
Immediately, we found an increase in malicious activity using COVID-19 as a lure to commit cybercrimes by offering urgent information in phishing emails, selling fake “vaccines” and numerous other scams. (Example is shown above)
We remain committed to keeping our clients safe during this pandemic. To that end, we have created a package of detections related to COVID-19 based attacks, which consists of known threat actors, attack methodologies, and how they’re exploiting COVID-19. If you are a Managed Services Partner or have a subscription to Léargas, there is nothing you need to do. The package was deployed and you will receive pertinent alerts as necessary.
Should you not be a subscriber, please reach out to us for more information on gaining access to these preventative measures.
Lastly, we want to provide some additional recommendations:
Recommendations for Our Clients:
Security always starts with the basics. If you aren’t using Léargas, make sure your systems are patched and IDS/IPS signatures and associated files are up to date. Attackers rely heavily on unpatched and out-of-date network configurations.Keep applications and operating systems running at the current released patch level. If you aren’t sure how to do this, reach out. One of our engineers will share some helpful information to assist you.
Leverage Multi-Factor Authentication! We see more companies breached each day due to the lack of multi-factor authentication than any other attack strategy. With hundreds of data breaches a year, we don’t expect this to decline.
Regrettably, in times like these when so many of us are coming together, there are still a few that will try to tear us apart. Be Aware, keep alert, stay strong, stay together, but stay 6 feet apart, for now.
-PK