What is SOAR and how can it help you?
SOAR (Security Orchestration, Automation, and Response) is a technology that enables security teams to automate repetitive tasks, aggregate multiple security tools and technologies into one unified platform, and improve the speed and accuracy of incident response. It helps organizations to streamline their security operations and make them more efficient and effective.
SOAR and platforms such as Léargas Security can perform tasks such as:
- Automating routine and repetitive tasks, freeing up security teams to focus on more complex incidents.
- Integrating with other security tools, such as SIEMs, firewalls, and endpoint protection solutions, to gather data and automate incident response.
- Correlating and analyzing data to quickly identify potential threats and prioritize incidents.
- Providing a centralized and standardized incident response process to improve the speed and efficiency of response efforts.
- Documenting and reporting on security incidents to improve incident response and to meet compliance requirements.
How does this differentiate from a SIEM?
SIEM stands for Security Information and Event Management, and is a type of software that collects and analyzes security data from various devices on a network to provide a centralized view of security events and to identify potential security threats. SIEMs help organizations to comply with security regulations, detect and respond to security incidents, and monitor the security posture of their networks.
SIEM and SOAR are both security technologies, but they serve different purposes and have different focuses.
SIEMs are designed to collect, store, and analyze security-related data from various sources such as network devices, servers, and applications. The goal of SIEMs is to provide a centralized view of security events and to help detect and respond to potential security threats.
Léargas Security, on the other hand, is designed to automate and orchestrate security-related processes such as incident response, threat hunting, and vulnerability management. Léargas Security provides a platform for security teams to automate repetitive tasks, standardize incident response procedures, and improve the overall efficiency of the security operations.
In summary, organizations may choose Léargas Security that leverages SOAR technology over a SIEM, because Léargas Security offers a more comprehensive and integrated approach to threat detection and response that covers multiple environments, while other platforms are limited to a narrower scope of security events and data.
 The leading question around the Cybersecurity community has been, “Will ChatGPT and OpenAI change Cybersecurity?“.
The leading question around the Cybersecurity community has been, “Will ChatGPT and OpenAI change Cybersecurity?“.
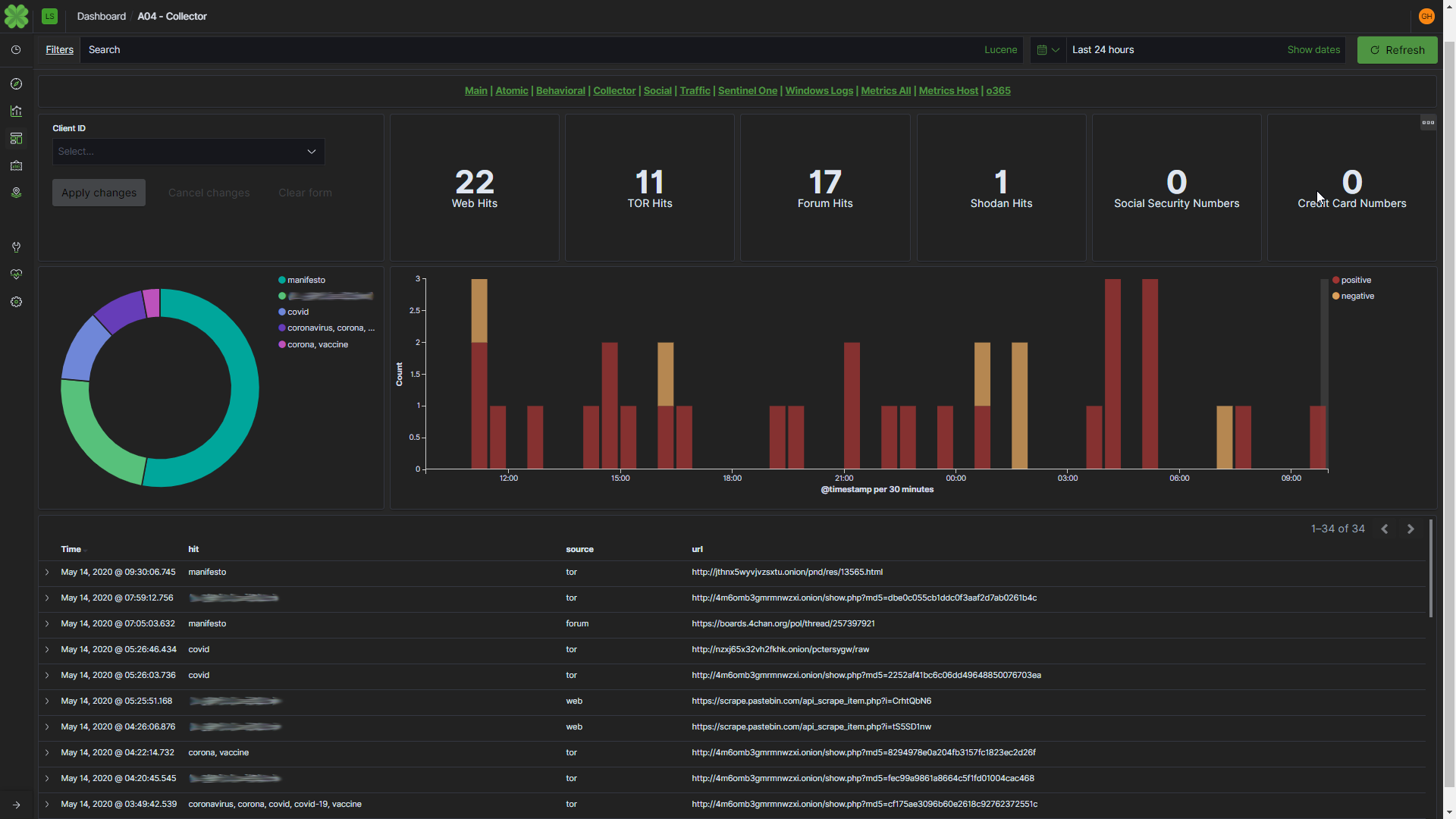
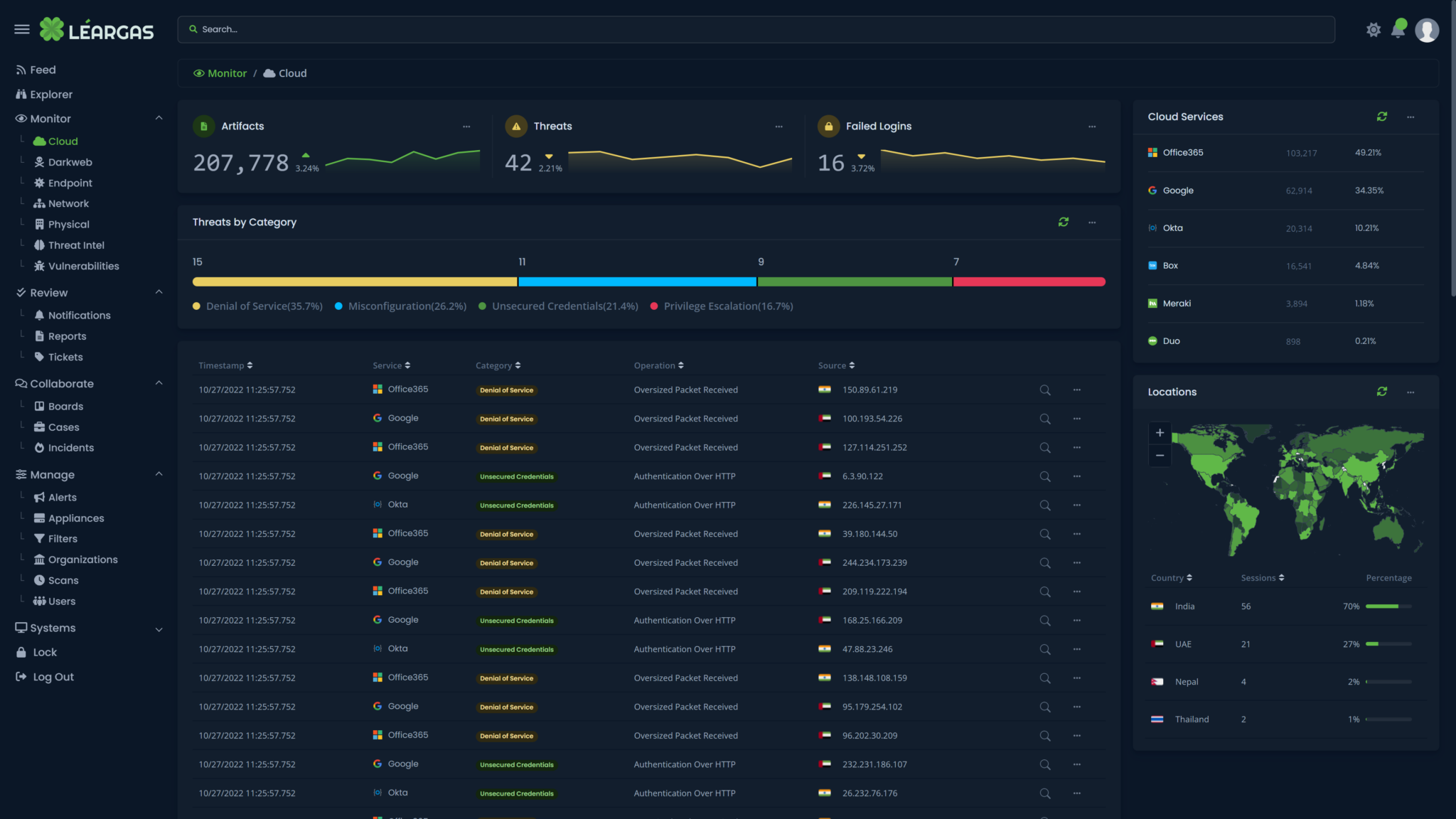
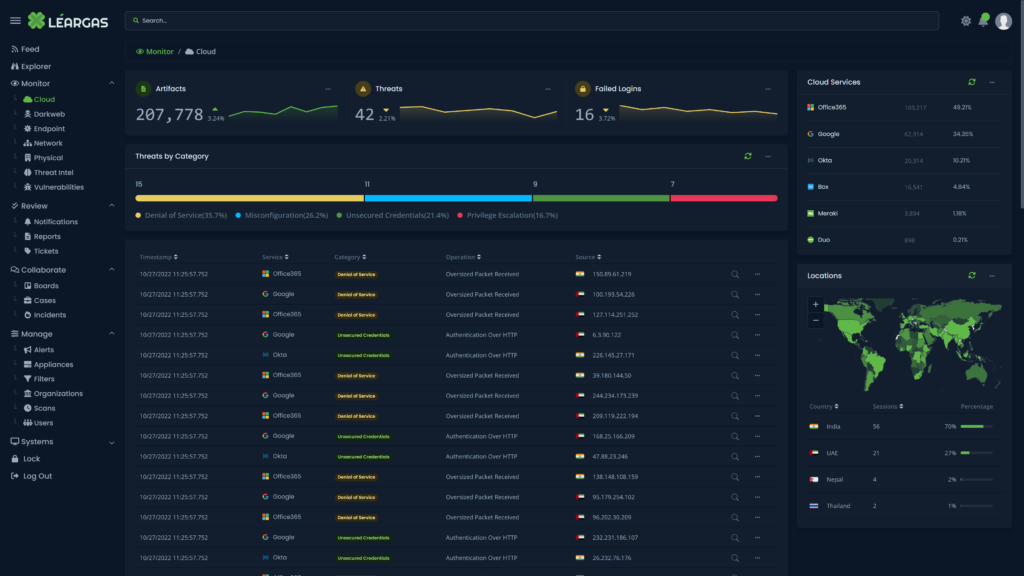 Data leak detection is a technology that helps organizations identify and prevent the unauthorized disclosure of sensitive or confidential information. Léargas automates this process, by leveraging artifacts collected from live network traffic, and automatically scouring data leak sites for those artifacts. Using Natural Language Processing, discovery of data leaks can extend to nearly any part of the open web and dark web, even into social media.
Data leak detection is a technology that helps organizations identify and prevent the unauthorized disclosure of sensitive or confidential information. Léargas automates this process, by leveraging artifacts collected from live network traffic, and automatically scouring data leak sites for those artifacts. Using Natural Language Processing, discovery of data leaks can extend to nearly any part of the open web and dark web, even into social media.
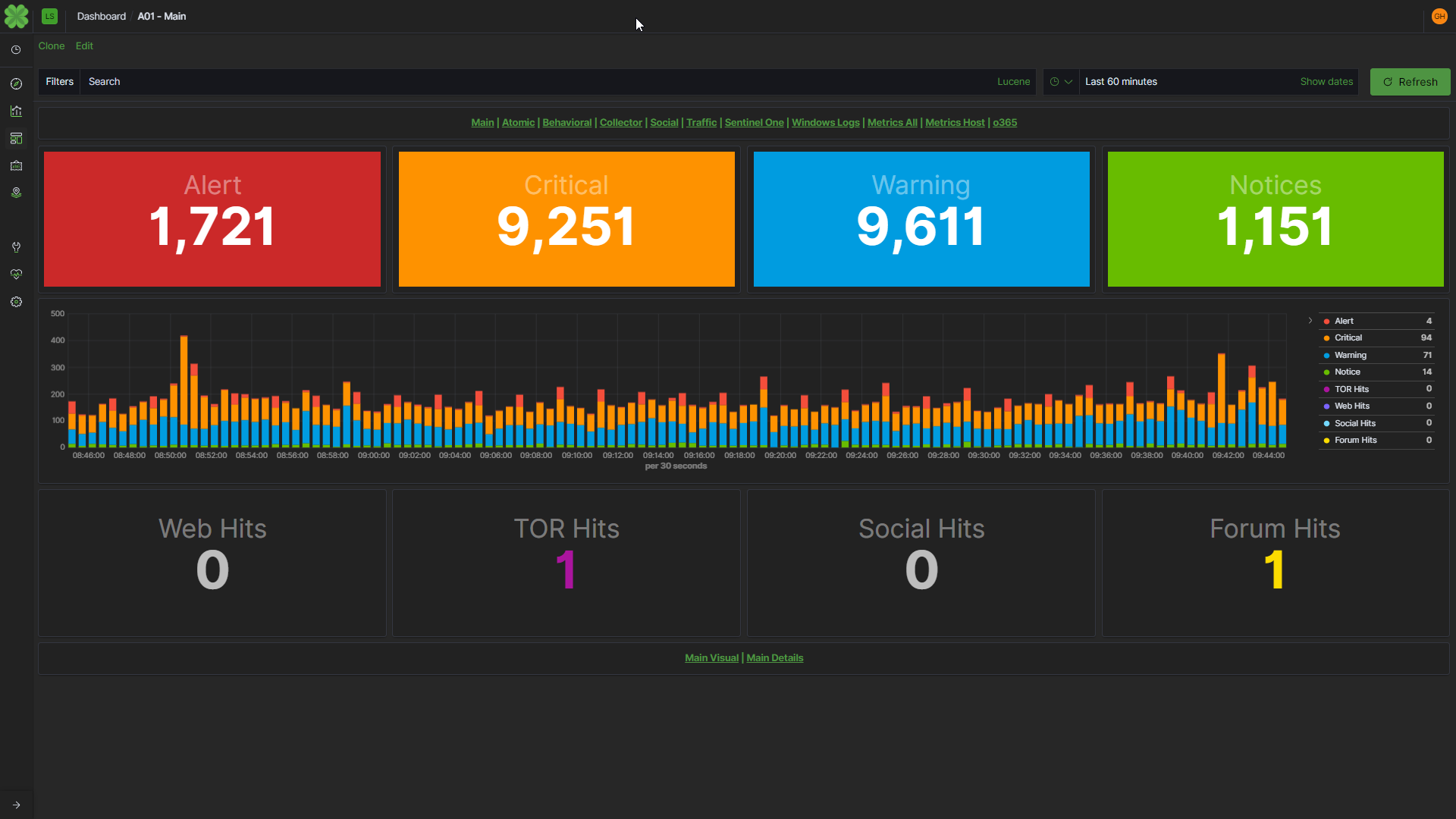
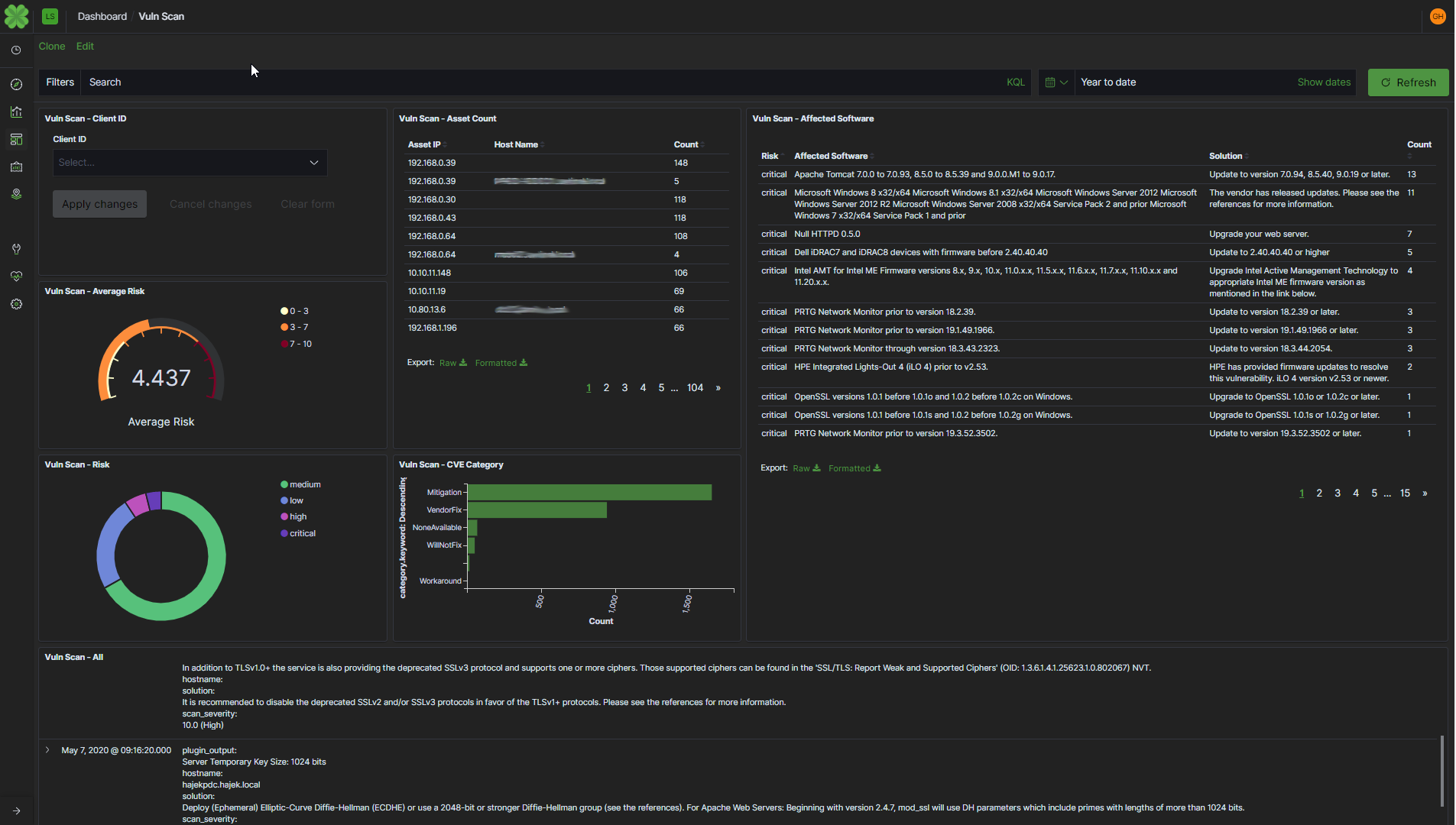 Léargas Vulnerability Telemetry
Léargas Vulnerability Telemetry